Abstract
Vehicular Ad hoc NETwork (VANET) is a multi-hop and high-speed mobile wireless communication network. In order to realize the security authentication of the information transmission between vehicle nodes in vehicular ad hoc networks, a certificateless aggregate signature scheme is designed. The proposed scheme uses certificateless cryptography, which eliminates the complex maintenance cost of certificate and solves the problem of key escrow. Communicating through pseudonyms and nodes around the roadside units generated, the conditional privacy protection is achieved for vehicle users. Then, the efficiency of the scheme is analyzed, and the relationship between the traffic density in VANETs environment and the time delay of message verification is simulated. The results show that the scheme satisfies the message authentication, anonymity, unforgeability and traceability, as well as the higher communication efficiency and the shorter delay of message verification, which is more suitable for dynamic vehicular ad hoc network environment.
Keywords: Vehicular ad hoc NETwork, aggregate signature, certificateless cryptosystem
1. Introduction
As the basis of future intelligent transportation, VANET provides a very important network environment for vehicle-to-vehicle communication, which can effectively solve the problems of road safety, traffic management and traffic congestion. It is a research direction that scientists are keen on at present. The on-board network is mainly composed of on-board units (OBU) installed on the vehicle and road-side units (RSU) deployed on the infrastructure around the road. Users communicate through vehicles-to-vehicle (V2V) and between vehicles and infrastructure (Vehicle-to-Infrastructure, V2I) to share information and access various services provided by nearby infrastructure [1]. The network model is shown in Figure 1 .
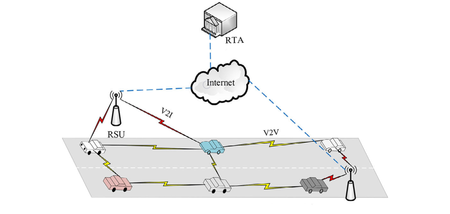
|
| Figure 1. The network model of VANETs (Source [10] |
Due to its own characteristics, such as resource limitation, high-speed movement of nodes, and communication delay should be short enough, the VANETs make their security issues very fragile, including eavesdropping, tampering, tracking user privacy, etc. [2]. If the messages in the vehicular network cannot be authenticated in a timely manner, the packet loss rate will increase, resulting in poor communication efficiency. Therefore, reducing the delay of message verification is a key requirement of the vehicle network for the efficiency of the authentication protocol. On the other hand, vehicle users are not willing to let their privacy and other sensitive information be illegally tracked and maliciously analyzed. When a traffic accident occurs or the owner commits a crime, the law enforcement authorities should be able to retrieve or track the owner’s information to reveal their identity, which is called conditional privacy protection [3].
Digital signatures can provide non-repudiation,authentication and integrity of messages. In the communication of the vehicle network with high traffic density, each RSU or traffic control center needs to verify a large amount of vehicle information, which will cause a large amount of calculation overhead. But in many cases, these calculations must be done in a resource-constrained environment with low bandwidth and low storage space. Aggregate signature is a hot spot that has been paid attention in recent years [4]. Using aggregation signature in VANET can greatly reduce the burden of RSU (Roadside unit). The signature based on the traditional PKI (Public Key Infrastructure) is based on the certificate system. CA (Certificate Authority) needs to bind the user and his public key, and the cost of managing and protecting certificates is very large, which is not suitable for the vehicle network. Identity-based aggregate signatures can avoid complicated certificate problems and can be applied to wireless networks and other fields [5-10]. But, that exits a key escrow problem in the identity-based aggregation signature scheme. The key generation center holds each user's private key, and there is a security problem of maliciously forging the signature. In recent years, some effective certificateless aggregation signature schemes have been proposed [11-20], which are provably secure in random predictions, but its high computational cost makes it unsuitable for dynamic wireless networks, such as VANETs. Horng et al. [3] proposed a privacy preserving aggregation signature model, which is based on certificateless cryptography. However, it has been proved that their scheme is not safe for malicious KGC. However, the authors themselves have always claimed that their scheme is provably secure and can resist adaptively choosing message attack. But, in fact, their scheme is insecure against a malicious-but-passive KGC under existing security model. In 2016, Nie et al. proposed a distributed certificateless aggregation signature scheme [4], but it has not been well applied in VANETs and cannot resist signature forgery attacks. The scheme in [9] does not use the hash function mapped to the point, and does not use the bilinear pair, but there is an inherent key escrow problem. Lai et al. [18] proposed group handover authentication, which better realized the overhead of instruction delivery and reduced the delay, but with the increase of vehicle density and mobile speed, the communication cost may also increase. Liu et al. And Zhang et al. For the first time, the secure communication in heterogeneous vehicle network is realized, however their schemes require OBUs (On Board Units) with high computation power [19,20]. In 2020,Ikram Ali's scheme can also effectively protect conditional privacy, However, as in [9], there is a key escrow problem. So far, the authentication scheme suitable for vehicular network has not been solved satisfactorily.
In this paper, an effective certificateless aggregation signature scheme suitable for vehicle network is proposed. In our scheme, the vehicle generates a pseudonym through RSU and communicates with surrounding nodes through the pseudonym. When necessary, law enforcement authorities can track the true identity of vehicle users through pseudonyms, realizing conditional privacy protection. Not only that, the experimental results show that the delay of message verification in our scheme is relatively low, but the computational cost is not high.
2. Basic theory and definition
2.1 Bilinear pair
Let be a secure parameter, be a -bit prime number, is a cyclic addition group of order generated by , is a cyclic addition group of order generated by , and has the same order cyclic multiplication group. Let the discrete logarithm problem in groups , , be a difficult problem. The mapping is called a bilinear pair, if satisfies the following properties:
- Bilinearity: For arbitrary , satisfy ;
- Non-degenerate: ;
- Easy to calculate properties: There is an effective algorithm to calculate .
In the above definition, if , the mapping is called an asymmetric bilinear pair; if , the mapping is called a symmetric bilinear pair which can be seen as a special case of asymmetric bilinear pairs. The bilinear map can be defined by Weil pairs or Tate pairs on a Special elliptic curve called hyper-singular curve on a finite field.
2.2 Aggregate signature
Aggregate signature is a variant of digital signature, which has the function of aggregation. That is to say, given users to individual signatures of messages , the generator of aggregate signature can aggregate these individual signatures into a unique short Signature . Furthermore, given the aggregate signature, the identity of the participating signers, and the original message , it can believe that the user signed the message . Let AS={Setup, Key, Sign, Verify, AggS, AggV} be a six-tuple of polynomial time algorithm, where Setup, Key, Sign and Verify are common signature algorithms. The remaining algorithms are described as follows:
- AggS:The algorithm of aggregate signature generation implements at least three sub-functions: First, it can implement ordinary signature functions. Secondly, it can realize the aggregation function of message vector group , user vector group and individual signature vector group . Finally, it can aggregate and add new individual signatures.
- AggV: The algorithm of aggregate signature verification. Assuming that each user owns a private key and a public key ,
- if
- ,
- It outputs "True", otherwise it outputs "False".
Aggregate signatures can also support incremental aggregation, that is, signatures , can be aggregated into , and then can be aggregated with to . The schematic diagram of the principle of aggregate signature is shown in Figure 2 .
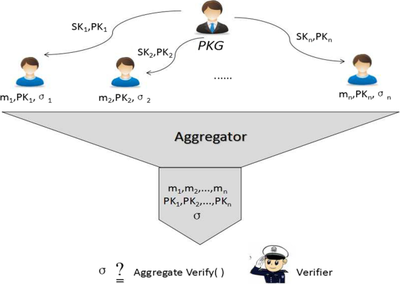
|
| Figure 2. Schematic diagram of aggregate signature |
Aggregate signatures can provide security services such as identity authentication, data integrity, and non-repudiation. In aggregate signatures, aggregation and signature are combined into one step, and the efficiency advantage is very obvious. Compress the signatures of any number of users into one signature, which greatly shorten the length of signature, and also reduce the network bandwidth requirements for transmitting signatures. Simplify the verification of any numbers of signatures to one verification, greatly reducing the workload of signature verification, so aggregate signatures greatly improve the efficiency of signature verification and transmission.
3. Design of certificateless aggregate signature scheme
Generally, the certificateless aggregate signature is composed of a key management center PKG, a signer, a signature aggregator, and a signature verifier. The scheme is composed of algorithms {System initialization, Key generation, Sign, Verify, Aggregate, Batch verification}. In addition to the above steps, the certificateless aggregation signature algorithm based on the VANETs designed in this paper also includes the vehicle registration algorithm, pseudonym generation algorithm and message verification algorithm. The specific description is as follows:
3.1 System initialization
Input the security parameter , the key management center KGC selects the additive cyclic group and the multiplicative cyclic group whose order is prime , and defines the bilinear mapping , and selects the generator of group . Then KGC randomly selects the master key , and calculates the public key of KGC, finally selects the secure hash function . The message set . Each RSU selects its secret value and calculates the public key , then send to KGC. The parameter list of the system is disclosed as follows:
3.2 Vehicle registration algorithm
The algorithm is executed by the Road and Transport Authority (RTA). For each vehicle user whose identity information is , in order to protect their privacy, RTA generates their false identity . RTA selects hash function and calculates . When law enforcement agencies want to track down vehicles that are responsible, RTA can show the true identity of the vehicle.
3.3 Key generation algorithm
KGC executes this algorithm. KGC inputs the parameter list , master key , and identity to calculate part of the private key of the vehicle user. The vehicle user can determine the correctness by verifying whether is true, because
The algorithm generates the secret value and public key of the vehicle user in VANETs, and once the vehicle travels to a new area, the new RTA can update the user's false identity. The user randomly selects a secret value and calculates its public key .
3.4 Pseudonym generation algorithm
The algorithm is executed by the roadside unit RSU. RSU inputs the identity of the vehicle user and parameter , and randomly chooses , then calculates
|
|
(1) |
|
|
(2) |
|
|
(3) |
Finally, RSU outputs the pseudonym
|
|
(4) |
3.5 Signature algorithm
To sign the outgoing message , the vehicle user needs to perform the following calculation process. randomly chooses , and calculates
|
|
(5) |
|
|
(6) |
|
|
(7) |
|
|
(8) |
and outputs the signature of this message .
3.6 Verification algorithm
Inputs the signature of this message , Public key , Partial pseudonym and parameter . The signature verification process needs to calculate the following values:
|
|
(9) |
|
|
(10) |
|
|
(11) |
If the equation holds, the signature is valid, otherwise the signature verification fails. The correctness is proved as follows:
3.7 Aggregate signature algorithm
After inputs the signatures of vehicle users , the aggregator outputs signature , where , , .
3.8 Batch verification algorithm
After receiving the aggregated signatures of users, the RSU verifies through the following steps:
|
|
(12) |
|
|
(13) |
|
|
(14) |
If the above equation is true, it indicates that the aggregation signature is valid, otherwise the signature verification fails.
4. Analysis of security and efficiency
We compare the aggregate signature scheme proposed in this paper with several schemes currently used in VANET. In contrast, the verification algorithm of scheme in [4] requires a large computational cost and cannot resist signature forgery attacks. Schemes in [19,20] have high computational efficiency, but they do not satisfy the traceability of signatures. Moreover, schemes in [9,10] are identity-based cryptosystems and suffer from inherent key escrow problem. In addition to satisfying the authentication of messages and the unforgeability of signatures, the scheme proposed in this paper has the following two characteristics.
4.1 Anonymity
Every vehicle user needs to register at the RTA of the Road Traffic Administration. RTA uses the hash function to associate the user ’s real and false , while the roadside unit RSU selects the random number as the false . A pseudonym was generated. Therefore, no one except RSU can associate the user's false and pseudonym , and no one except RTA can associate the user's real and false . Therefore, the scheme proposed in this paper satisfies the anonymity of vehicle users.
4.2 Traceability
In the signature scheme proposed in this article, once the verification algorithm fails or the vehicle user commits a crime, the RSU can submit the false identity of the vehicle user to RTA. The RTA queries the registration information of the vehicle user to track the corresponding true identity . In the event of disputes or doubts, RTA uses the one-way nature of the hash function to verify the true identity of malicious vehicle users by calculating , which enables traceability of illegal vehicle users. Table 1 gives a comparison of the security of several schemes. It can be seen that the scheme in this paper has the above-mentioned excellent properties.
| [4] | [9] | [10] | Our scheme | |
|---|---|---|---|---|
| Communication mode | V2I | V2I | V2V | V2I |
| Authentication | Yes | Yes | Yes | Yes |
| Anonymity | Yes | Yes | No | Yes |
| Traceability | No | No | Yes | Yes |
| Resist forgery attack | Yes | Yes | Yes | Yes |
| Certificateless | Yes | No | No | Yes |
We give a comparison of the calculation costs of several certificateless aggregate signature schemes currently used in VANET, as shown in Table 2. We only select four of the more time-consuming operations. Let , , , and represent the operation of a bilinear map, a scalar multiplication, a modular exponentiation, and a point multiplication respectively in G. These four operations run on an Intel i7 3.07GHz machine with approximately 3.21ms, 1.79ms, 0.442ms, 1.9ms. It can be seen that when there is more traffic, the calculation cost of our scheme is relatively low. The calculation time of other operations such as the hash function is very small and can be ignored. In the table, Sync represents the normal transmission mode, Ad hoc represents the ad hoc network transmission mode, and represents the number of vehicle users.
| Scheme | Type | Signature | Verification | Aggregate verification |
|---|---|---|---|---|
| [4] | Sync | 3B | 4B+S | 4B+nS |
| [19] | Adhoc | 2B | 2B+3P | 2B+3nP |
| [20] | Adhoc | 3E | 4E | (3n+1)E |
| Our scheme | Adhoc | 3S | 3B+2S | 3B+2nS |
We simulated the proposed scheme in windows + OPNET IT Guru release 9.1.a and compared several VANET-based certificateless aggregate signature schemes, as shown in Figure 3. By comparing the traffic flow entering the same roadside unit RSU with the verification delay time, we can see that when the traffic load increases, our scheme verifies the most signatures, that is, the information loss rate is the lowest.
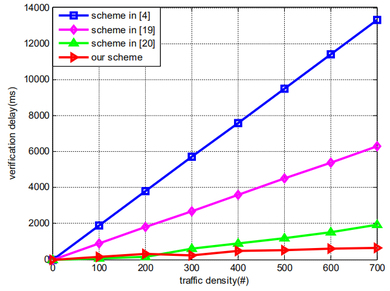
|
| Figure 3. Traffic density versus verification delay |
5. Conclusion
The algorithm of aggregate signature aggregates the signatures of many different users into one signature, and only needs to verify the aggregated signature to determine whether the received signature is legal, which greatly improves the efficiency of message verification. This advantage makes it self-organized in the vehicle. It has good application value in the network. The secure and effective certificateless aggregate signature scheme proposed in this paper has the double advantages of certificateless cryptosystem and aggregate signature. The scheme in this paper effectively combines the privacy protection of vehicle users and the traceability of illegal users, so-called conditional privacy protection. According to the results of simulation, compared with other existing solutions, the solution in this paper has the advantages of low communication cost, low calculation cost and short verification delay, so it is more suitable for resource-constrained network environments such as VANETs.
Acknowledgement
This work has been partially supported by Outstanding Young Talent Program in Universities of Anhui (grant no. gxyqZD2016330).
Conflicts of Interest
The authors declare no conflict of interest.
References
[1] Liu Z., Liu J., Wu Q., et al. Secure and efficient distributed pseudonym generation in VANET. Journal on Communications, 36(11):33-40, 2015.
[2] Lu Z., Qu G., Liu Z. A survey on recent advances in vehicular network security, trust, and privacy. IEEE Trans. Intel. Transp. Syst., 20(2):760–776, 2019.
[3] Horng S.J., et al. An efficient certificateless aggregate signature with conditional privacy preserving for vehicular sensor networks. Information Sciences, (317):48-66, 2015.
[4] Nie H., Li Y., Chen W., et al. NCLAS: A novel and efficient certificateless aggregate signature scheme. Security & Communication Networks, 9(16):3141-3151, 2016.
[5] Hongzhen D.U. An efficient and secure aggregate signature scheme for vehicular ad hoc network. Henan Science, 34(4):481-485, 2016.
[6] Shen L., Ma J., Liu X., et al. A provably secure aggregate signature scheme for healthcare wireless sensor networks. Journal of Medical Systems, 40(11):244-247, 2016.
[7] Shen L., Ma J., Liu X., et al. A secure and efficient ID-based aggregate signature scheme for wireless sensor networks. IEEE Internet of Things Journal, 4(2):546-554, 2017.
[8] Iwasaki T., Yanai N., Inamura M., et al. Tightly-secure identity-based structured aggregate signature scheme under the computational Diffie- Hellman assumption. 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, pp. 669-676, 2016.
[9] Wang S., Yao N. LIAP: A local identity-based anonymous message authentication protocol in VANETs. Comput. Commun., 112:154–164, 2017.
[10] Ali A., Li F. An efficient conditional privacy-preserving authentication scheme for vehicle to infrastructure communication in VANETs. Vehicular Communications, 22:1-15, 2020.
[11] Tu H., He D., Huang B. Reattack of a certificateless aggregate signature scheme with constant pairing computations. The Scientific World Journal, 2014:1-10, 2014.
[12] Shim K.A. On the security of a certificateless aggregate signature scheme. IEEE Communications Letters, 15(10):1136-1138, 2011.
[13] He D., Tian M., Chen J. Insecurity of an efficient certificateless aggregate signature with constant pairing computations. Information Sciences, 268:458-462, 2014.
[14] Zhang Y., Li C., Wang C., et al. Security analysis and improvements of certificate -less aggregate signature schemes. Journal of Electronics & Information Technology, 37(8):1994-1999, 2015.
[15] D. H., Huang M., Wen Q.. Efficient and Provably-Secure certificateless aggregate signature scheme. Acta Electronica Sinica, 41(1):72-76, 2013.
[16] Shen H., Chen J., Shen J., et al. Cryptanalysis of a certificateless aggregate signature scheme with efficient verification. Security & Communication Networks, 9(13):2217-2221, 2016.
[17] Wang L., Chen K., Long Y., et al. Cryptanalysis of a certificateless aggregate signature scheme. Security & Communication Networks, 9(11):1353-1358, 2016.
[18] Lai C., Zhou H., Cheng N., Shen X.S. Secure group communications in vehicular networks: a software-defined network-enabled architecture and solution. IEEE Veh. Technol. Mag., (12):40–49, 2017.
[19] Liu J., Yu Y., Zhao Y., Jia J., Wang S. An efficient privacy preserving batch authentication scheme with deterable function for VANETs. International Conference on Network and System Security, Springer, pp. 288–303, 2018.
[20] Zhang X., Mu L., Zhao J., Xu C. An efficient anonymous authentication scheme with secure communication in intelligent vehicular ad-hoc networks. KSII Trans. Int. Inf. Syst., 13(6):3280–3298, 2019.
Document information
Published on 27/08/20
Accepted on 19/08/20
Submitted on 20/06/20
Volume 36, Issue 3, 2020
DOI: 10.23967/j.rimni.2020.08.002
Licence: CC BY-NC-SA license