Abstract
This study aims to analyze how privacy concerns about the Internet have an impact on the consumers intention to make online purchases. A research model was developed establishing that this impact takes place via the connection of privacy concerns with the theories of trust and risk, the theory of planned behaviour and the technology acceptance model. The empirical study was based on an online survey that collected data from 900 individuals. The results confirmed the acceptance of all proposed hypotheses and the overall validation of the research model. Implications and further research suggestions are presented.
JEL classification
M31;L81
Keywords
Privacy concerns;E-commerce;Online purchasing behaviour
1. Introduction
In recent years, the number of electronic commerce (EC) users increased significantly. According to Eurostat (2014), between 2004 and 2013, the penetration rate of EC increased by 150% in just the European Union (27 countries). However, despite this increase, the proportion of consumers that purchase online is still reduced in most European countries. In 2013, only 38% of European Union consumers made online purchases in the last 3 months and only 14% of firms’ turnover is generated from EC. Searching the reasons for this phenomenon, we note that privacy concerns about personal information are the second most important motivation for non-adoption of EC by European Union consumers, just after security concerns.
The privacy of personal information is recognized as a fundamental theme in marketing literature in both offline (Jones, 1991) and online contexts (Miyazaki & Fernandez, 2000). However, the literature has underestimated the role of privacy concerns in EC context, since this variable has been introduced in online shopping models that are, in essence, focused on trust (Chen & Barnes, 2007) or on perceived risk (Van Slyke, Shim, Johnson, & Jiang, 2006). Moreover, the published studies have focused mainly on the direct impact of privacy concerns in online purchase intention (Eastlick, Lotz, & Warrington, 2006) or in online actual purchase (Brown & Muchira, 2004). Thus, these studies do not provide a theoretical framework that is robust enough to explain how privacy concerns exerts their influence on relevant variables of consumer behaviour that precede the pre-purchase or purchase decision. We consider this fact a gap in the literature that should be overcome.
As such, the research question that guides this study is the following: how privacy concerns in the Internet influence online purchasing intention? This paper aims to develop and validate an online consumer behaviour model that pursues the following specific objectives: (1) The identification of variables that mediate the relationship between privacy concerns and online purchasing intention; (2) The recognition of dependency relationships that are established between privacy concerns and the mediating variables; (3) The recognition of dependency relationships that are established between the mediating variables; (4) The recognition of dependency relationships that are established between the mediating variables and the online purchasing intention.
The paper is organized as follows. First a literature review on privacy, trust, perceived risk and consumer behaviour models is presented. Then, the research hypothesis and the resulting research model are presented, highlighting the role of mediating variables of the relationship between privacy concerns and online purchasing intention. The next chapter is dedicated to the discussion of the methodology used, which is followed by the description of results. Finally, discussion of results, theoretical and managerial implications, limitations and future research suggestions are presented.
2. Literature review
2.1. Privacy concerns
The information privacy was initially defined as the individuals ability to control the conditions under which his/her personal information is collected and used (Westin, 1967).
The first reference in the literature to an instrument for measuring privacy concern about personal information is the scale called “Concern for Information Privacy” developed by Smith, Milberg, and Burke (1996). In this work, the authors developed a theoretical framework that conceptualizes privacy concerns about personal information in the following five key dimensions: collection, which refers to the concern that large amounts of personal data are collected and stored; unauthorized secondary internal use, with regard to the concern that the information collected for a particular purpose is used by the organization for other purposes without the consent of the individual; unauthorized secondary external use, which refers to the concern that the information collected for a particular purpose is used for another purpose after its disclosure to an external organization; improper access, which refers to the concern that personal data be made available to persons who are not properly authorized to do so; errors, pointing to concerns that the protection against accidental or deliberate errors in personal data would not be appropriate.
The protection of information privacy in EC began attracting the attention of the official authorities including the Federal Trade Commission (FTC) in the United States of America. This entity has developed a set of guidelines called Fair Information Practices (Gillin, 2000) consistent with previous research, namely the study of Smith et al. (1996). In line with this study, the FTC guidelines incorporated rules about the collection of information by sellers, the correction of errors in the information collected, the communication to the consumers about the use of their information for other purposes than the initial and the prevention of unauthorized access to information. Similarly, the FTC guidelines were consistent with the studies of Culnan and Armstrong (1999) and Hoffman, Novak, and Peralta (1999), establishing that the sellers must provide consumers with control over all aspects related to the collection and use of information.
Based on the guiding principles of the FTC, Sheehan and Hoy (2000) identified three underlying dimensions of online privacy concern: control, short-term relationship and long-term relationship. The control dimension refers to the users degree of control over the collection and use of his/her personal information. The short-run relationship dimension is related to the individuals concern with the type of information that provides online, as well as the counterpart received in exchange of that information. The long-term relationship dimension suggests that the consumer and the organization already have an established relationship, pointing to the level of individuals concern arising from the online communication and interaction from both.
In order to maximize the potential of EC, it is especially important to realize in detail consumers’ online information privacy concerns. Despite a few pioneering studies addressing the issue of online privacy in general, such as Miyazaki and Fernandez (2000) and Sheehan and Hoy (2000), no studies have provided a specific theoretical framework to privacy concerns in the context of the Internet.
The exception arises from the study of Malhotra, Kim, and Agarwal (2004), which presents a conceptual framework and develops a specific scale to online privacy concerns. The authors argue that Internet users information privacy concerns focus on three major dimensions: collection, control and awareness. Collection is defined as the individuals level of concern about the amount of personal data possessed by others, in comparison with the benefits received. In turn, control reflects the ability of consumers to be heard on how personal data is used and on its access, modification and deletion. Finally, awareness is reflected in the individuals degree of information about the organizations privacy practices.
The literature has shown considerable interest in issues related to online privacy, having incorporated this construct in numerous studies of consumer behaviour, several of which are anchored in the theory of planned behaviour (TPB) and in the technology acceptance model (TAM). These studies show that privacy concern has a positive influence on perceived risk (e.g. Van Slyke, Shim, Johnson, & Jiang, 2006) and a negative influence on trust (e.g. Eastlick et al., 2006; Liu et al., 2005 ; Van Dyke et al., 2007), on intention to buy online (e.g. Liao et al., 2011; Midha, 2012 ; Taylor et al., 2009) and on online buying behaviour (e.g. Dinev et al., 2006a ; Dinev et al., 2006b).
2.2. Trust
Trust in the online environment poses a number of challenges and contains specificities that cannot be ignored. Due to the unique characteristics inherent to the EC environment, such as the inability to directly touch and see the product and the lack of face to face interaction, consumers feel a lot of uncertainty and a huge risk in their online purchasing decisions (Hoffman et al., 1999). The resulting lack of trust leads to the hesitation of many consumers in expressing the behaviours that are necessary to a wider dissemination of EC, such as sharing personal information and make online purchases (McKnight, Choudhury, & Kacmar, 2002). Thus, the lack of consumer trust is assumed as a strong barrier to the growth of EC.
In a study directed to the individual consumers intention to buy online, Jarvenpaa, Tractinsky, and Vitale (2000) defined trust as the belief or expectation that the consumer can take the word or promises of the retailers and expect that they will not take advantage of its vulnerability.
Lee and Turban (2001) developed a theoretical model that establishes that online trust depends on four major determinants: trustworthiness of the Internet merchant, conceptualized in terms of its ability, integrity and benevolence; trustworthiness of the Internet shopping medium, defined in terms of technical competence, reliability and medium understanding, Internet shopping contextual factors, such as the effectiveness of third party certification and of security infrastructure, and other factors, such as size of Internet merchant, demographic variables, and prior related experience.
Pavlou (2003) defines trust in the context of business-to-consumer EC as the belief that allows consumers to willingly become vulnerable to online retailers, after taking into consideration their characteristics and the environment in which transactions are performed. The literature has shown considerable attention to online trust, having incorporated this construct in numerous studies of consumer behaviour, many of which are based on the TPB and on the TAM. These studies have shown the negative influence of trust on perceived risk (e.g. Kim et al., 2009; Teo and Liu, 2007 ; Van Slyke et al., 2006) and the positive influence on attitude towards online buying (e.g. Ha and Stoel, 2009; McCole et al., 2010 ; Palvia, 2009), on intention to buy online (e.g. Kim et al., 2009; Kim et al., 2010 ; Liao et al., 2011) and on online buying behaviour (e.g. Dinev et al., 2006b).
2.3. Perceived risk
The online shopping environment has a set of specific characteristics that result in a perceived risk by the consumers with different characteristics of the offline context. It is known that the perception of risk is a major obstacle to the growth of EC and its consolidation as a source of competitive advantage for organizations (Benbasat & Barki, 2007).
Lim (2003) adopts an innovative approach in the identification of the dimensions of perceived risk. Rather than following the traditional approach based on the risk consequences, he adopts the perspective of the sources of perceived risk, suggesting the following four dimensions: technology risk, vendor risk, consumer risk and product risk. Perceived technology risk is the degree to which individuals believe that if they make online purchases, they will suffer losses caused by the Internet and its technology infrastructure, such as download delays, search problems, or security weaknesses. Vendor perceived risk is the degree to which individuals believe that if they make online purchases, they will suffer losses caused by Internet vendors, like the non- delivery of products and the unauthorized use of consumers personal information. Consumer perceived risk is the degree to which individuals believe that if they make online purchases, they will suffer losses caused by social pressure, such as negative comments from family, friends or colleagues about a product purchased online. Product perceived risk is the degree to which individuals believe that if they make online purchases, they will suffer losses caused by the products acquired. These losses may be originated by the lack of information available on the website, doubts about the quality of the products, and the purchase of defective products, or that do not correspond to consumer expectations.
Glover and Benbasat (2011) proposed a tri-dimensional typology of general perceived risk in the context of EC based on its causes. The first dimension was labelled as failure to gain product benefit risk and occurs when the consumer doesn’t obtain from the online retailer the benefits expected of the product. The second dimension was labelled as information misuse risk and may occur when the consumer suffers a loss of personal information privacy during an online purchase. The third dimension was labelled as functionally inefficiency risk and occurs if consumers waste time, money, or effort in making an online purchase, losing the resources with which hoped to make a gain.
Extensive research has been produced incorporating the construct of online perceived risk in studies of consumer behaviour, many of which are based on the TPB and the TAM. These studies have shown that perceived risk has a negative effect on the attitude towards online buying (e.g. Crespo et al., 2009; Glover and Benbasat, 2011 ; Teo and Liu, 2007), on the intention to buy online (e.g. Crespo et al., 2009; Li et al., 2011 ; Liao et al., 2011) and on the online buying behaviour (e.g. Dinev et al., 2006b ; Park et al., 2004).
2.4. Consumer behaviour models
2.4.1. Theory of planned behaviour
The theory of planned behaviour (TPB) is an extension of the theory of reasoned action (TRA) (Ajzen & Fishbein, 1980; Fishbein & Ajzen, 1975), which aims to address the limitations of the latter model in dealing with behaviours over which the individual had an incomplete volitional control (Ajzen, 1991). Like the TRA, the TPB has the overall objective to predict and explain human behaviour in specific situations.
According to the TPB, behaviour is explained by the behavioural intention and perceived behavioural control. The behavioural intention captures the motivational factors that influence the behaviour, giving an indication of the magnitude of the effort that the individual is willing to do to perform the behaviour. The perceived behavioural control, which is a new construct of the TPB compared to the TRA, can be defined as the individuals perception of the ease or difficulty to perform the behaviour under study.
With regard to behavioural intention, the TPB provides that its determinants are not only the attitude towards the behaviour and the subjective norm as in the TRA, but also the perceived behavioural control. The attitude towards the behaviour is a favourable or unfavourable evaluation of the individual regarding the consequences of the behaviour. Subjective norm is the social pressure felt by the individual to perform or not perform the behaviour.
The TPB is one of the most used consumer behaviour models in the literature, and have been widely used in the context of online shopping behaviour (e.g. Lim and Dubinsky, 2005; Pavlou and Fygenson, 2006 ; Song and Zahedi, 2005).
2.4.2. Technology acceptance model
Based on the TRA, the technology adoption model (TAM) was developed with the generic purpose of explaining and predicting the use of information systems by end users. According to Davis, Bagozzi, and Warshaw (1989), TAM is assumed as a parsimonious and theoretically robust model that can be applied to the explanation and prediction of the adoption of a wide range of computer-based technologies by different populations of users. The model enables the tracking of the successive impact of external variables on beliefs, attitudes, intentions and behaviours of the individual, by integrating in the theoretical framework of TRA a small number of key variables derived from the literature on cognitive and affective determinants of technology adoption.
According to Davis (1989) and Davis et al. (1989), the TAM gives relief to two specific beliefs in the adoption of information technologies: perceived usefulness, defined as the individuals belief that the use of certain technology will improve its performance, and perceived ease of use, which refers to the individuals belief that the use of a particular technology will be free of effort.
In line with the TRA, TAM determines that the use of a given technology is explained by behavioural intention. In turn, the intention is jointly determined by attitude towards the use and perceived usefulness. The attitude is explained by both the perceived usefulness and the perceived ease of use. The TAM also sustains that the perceived ease of use is determined by the perceived usefulness. Finally, the perceived ease of use and the perceived usefulness can be influenced by external variables.
Thanks to its simplicity and ease of application, TAM has become one of the most used technology related behaviour models in the literature, and has been widely in the context of the adoption of EC (e.g., Crespo et al., 2009; Ha and Stoel, 2009 ; Palvia, 2009). In this field of research, TAM has been used in its original form and combined with other models of consumer behaviour, including the TPB. It is expected that a congregation of the TPB and the TAM is likely to increase the explanatory and predictive power of the online buying behaviour. The proposed research model will explore this possibility.
2.5. Endnotes
Based on the literature review, it is concluded that the concepts of privacy concerns, trust and perceived risk are interrelated and linked to the TPB and the TAM, which have been widely used, alone or together, in the context of online shopping behaviour. This conceptual framework is articulated in the following chapter, where will be explained in detail the construction of the research model.
3. Research model
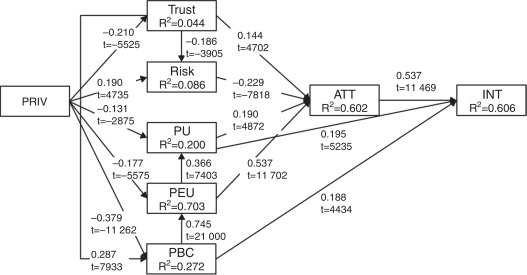
The proposed research model, depicted in Fig. 1, aims to understand how privacy concerns on the Internet exert their influence on online purchasing behaviour. According to the literature review, the conceptual framework of this study consists of privacy theories, trust theories, risk theories, which are inserted in the framework of the TPB and the TAM.
|
|
|
Fig. 1. Structural model. |
Under the trust-risk model, there is a broad consensus in the literature about the influence of personal characteristics on trust and risk beliefs (McKnight, Cummings, & Chervany, 1998). Privacy concerns can be seen as a personal characteristic that will ultimately influence how the individual perceives a situation where personal information is requested to accomplish an online transaction (Malhotra et al., 2004). Thus, a consumer with a high degree of privacy concerns is more likely to feel a low level of trust (Eastlick et al., 2006) and a high level of perceived risk within an online purchase (Van Slyke et al., 2006). Hence, the following hypotheses are proposed: privacy concerns on the Internet have a negative effect on trust in EC (H1a) and a positive effect on perceived risk of EC (H1b).
Moorman, Zaltman, and Deshpande (1992) argue that trust reduces perceived uncertainty and therefore perceived vulnerability. In the case of an online purchase, this means that it is expected that trust mitigates the perceived risk of the transaction (Pavlou, 2003). Therefore, the following hypothesis is proposed: trust in EC has a negative effect on perceived risk of EC (H2).
It is expected that an individual with high privacy concerns associate to online shopping activities a psychological burden, which reduces its levels of pleasure, namely, its intrinsic motivation (Davis, Bagozzi, & Warshaw, 1992). According to the study of Venkatesh, Cheri, and Morris (2002) in the context of technology adoption, intrinsic motivation has a negative impact on perceived usefulness and perceived ease of use. In this study, it is proposed that these relationships will occur on the adoption of EC. Thus, the following hypotheses are proposed: privacy concerns on the Internet have a negative effect on the perceived usefulness of EC (H3a) and on the perceived ease of use of EC (H3b).
Supported in TAM, we can assert that perceived ease of use is a determinant of perceived usefulness (Davis et al., 1989). Within EC, if the consumer develops the belief that saves time and effort when buying online, then the saved resources can be reallocated to other tasks, which represent an increase of the utility of EC (Ha & Stoel, 2009). Hence, the following hypothesis is proposed: perceived ease of use of EC has a positive effect on perceived usefulness of EC (H4).
A consumer with higher privacy concerns in the context of Internet will have a greater tendency to understand that not all conditions are satisfied to accomplish an online purchase. Thus, following Pavlou and Fygenson (2006), privacy concerns influence the facilitating conditions and thus have a negative impact on the perception of control over making online purchases. Therefore, the following hypothesis is proposed: privacy concerns on the Internet have a negative effect on perceived control over EC use (H5).
In the context of online consumer behaviour, trust mitigates uncertainty and thus acts as a facilitating condition with a positive impact on consumer perception of control over making online purchases (Pavlou & Fygenson, 2006). Thus, the following hypothesis is proposed: trust in EC has a positive effect on perceived control over EC use (H6).
In the path of Venkatesh (2000) study on technology adoption, it is proposed that higher consumers beliefs about their ability to buy online and the absence of barriers to accomplish transactions, conducts to a greater control over EC use. In turn, this increased control will lead consumers to associate a lower degree of difficulty to buy over the Internet. Hence, the following hypothesis is proposed: perceived control over EC use has a positive effect on perceived ease of use of EC (H7).
According to Ajzen (1991), TPB states that attitudes are a function of relevant beliefs to the individual. Within the EC, trust and perceived risk are beliefs that work, respectively, as key facilitators (Ha & Stoel, 2009) or inhibitors (Fenech & O’Cass, 2001) of the development of a positive evaluation of online purchasing results. Therefore, the following hypotheses are proposed: attitude towards the use of EC suffers a positive effect of trust in EC (H8a) and a negative effect of perceived risk of EC (H8b).
TAM introduces the concepts of perceived usefulness and perceived ease of use, arguing that these beliefs are fundamental in explaining and predicting attitudes (Davis et al., 1989). In the context of online purchasing behaviour, these relationships mean that the larger the consumers beliefs about the improved performance resulting from the EC use and its ability to make online purchases without effort, the better will be the individuals evaluation of the expected results of those transactions (Pavlou & Fygenson, 2006). Thus, the following hypotheses are proposed: attitude towards the use of EC suffers a positive effect of perceived usefulness of EC (H9a) and of perceived ease of use of EC (H9b).
TAM sustains that perceived usefulness is a determinant of intention to adopt a particular technology. In the field of online buying behaviour, the higher the consumers’ beliefs about the improved performance of purchase from the use of EC platforms, the greater the likelihood of these being used to make purchases online (Pavlou, 2003). Hence, the following hypothesis is proposed: perceived usefulness of EC has a positive effect on intention to use EC (H10).
Within the TPB, perceived behavioural control is a determinant of behavioural intention (Ajzen, 1991). It is expected that the higher the consumers beliefs about the control over making online purchases, the greater their intention to accomplish these transactions (Lwin & Williams, 2003). Therefore, the following hypothesis is proposed: perceived control over EC use has a positive effect on intention to use EC (H11).
Under the TPB and the TAM, it is known that the attitude towards behaviour is a fundamental determinant of behaviour intention (Ajzen, 1991 ; Davis et al., 1989). Within EC, it is also possible to assert that a better consumers’ evaluation on the results of making online purchases, will result on a higher likelihood of accomplish those transactions (Lwin & Williams, 2003). Thus, the following hypothesis is proposed: attitude towards the use of EC has a positive effect on intention to use EC (H12).
4. Methodology
The population of this study consists of Internet users residing in Portugal, aged between 16 and 74 years. The empirical study was conducted among a non-random sample of 900 respondents, which was removed from the largest online panel in Portugal. This panel belongs to Netsonda, a marketing research company that has a database with more than 147,000 registered users. In order to ensure that the various groups of the population were properly represented in the sample we used a process of quota sampling with a three-dimensional categorization based on three socio-demographic criteria: gender, age and educational level. The size of each quota was roughly proportional to the size of the respective group in the population. All respondents reported that they had made online purchases in the last 12 months. The composition of the collected sample is described in Table 1.
| Gender | Age group | Educational level | N | % |
|---|---|---|---|---|
| Male | 16–24 | Up to secondary education | 135 | 15.00 |
| Higher education | 5 | 0.56 | ||
| 25–54 | Up to secondary education | 221 | 24.56 | |
| Higher education | 79 | 8.78 | ||
| 55–74 | Up to secondary education | 25 | 2.78 | |
| Higher education | 19 | 2.11 | ||
| Female | 16–24 | Up to secondary education | 117 | 13.00 |
| Higher education | 15 | 1.67 | ||
| 25–54 | Up to secondary education | 148 | 16.44 | |
| Higher education | 110 | 12.22 | ||
| 55–74 | Up to secondary education | 16 | 1.78 | |
| Higher education | 10 | 1.11 | ||
| Total | 900 | 100 | ||
The questionnaire was developed from the adaptation of the scales presented in the studies of Dinev and Hart (2006) for privacy concerns, Pavlou (2003) for trust, Schlosser et al. (2006) for perceived risk and behaviour intention, Park et al. (2004) for perceived usefulness, Koufaris (2002) for the perceived ease of use, Song and Zahedi (2005) for perceived behavioural control and Lim and Dubinsky (2005) for attitude. Although the literature considers that privacy concerns, trust and perceived risk can be conceptualized as multidimensional constructs, we chose to use unidimensional scales that capture the major dimensions of those constructs so that the size of the questionnaire was not considered excessive by the respondents, decreasing the response rate. All items were measured with Likert scales of 7 points (1 = totally disagree; 7 = totally agree) which were extensively used on previous studies about EC use (e.g. Dinev and Hart, 2006; Lim and Dubinsky, 2005 ; Schlosser et al., 2006). The final version of the questionnaire is presented in Appendix 1.
A pre-test of the questionnaire was conducted among a convenience sample of 90 respondents, which aimed to assess the comprehension of questions, the format of the questionnaire, the response time, and the psychometric properties of the scales. Specific adjustments were made in the formulation of some questions following the feedback from the pre-test. All scales showed their unidimensionality, based on the results of the exploratory factor analysis, and adequate internal consistency, based on the results of the item analysis and Cronbachs alpha.
The final data collection was conducted through an online survey, to which all the elements of the sample were invited by e-mail.
We examined the common method bias by using Harmans single-factor test, as proposed by Podsakoff, MacKenzie, Lee, and Podsakoff (2003). This test was applied by conducting an exploratory factor analysis which resulted in 8 factors with no factor accounting for the majority of the variance, once the largest variance explained by a single factor was 19,126%. This suggests that no substantial amount of common method variance was present in our data set.
5. Results
Structural equation modelling with LISREL version 8.80 was used to validate the research model. The estimation method was robust maximum likelihood. It was adopted a two phases modelling strategy, following the indications of Gerbing and Anderson (1988), which consists in independent estimation and analysis of the measurement model and then the structural model.
The results obtained in the confirmatory factor analysis indicated an appropriate overall fit of the measurement model (χ2 = 1606.568, p = 0.000; χ2/df = 3.440, RMSEA = 0.0521, CFI = 0.985). The χ2 statistic indicates that the variance-covariance matrices observed and estimated differ considerably, however, it is known that this indicator penalizes more complex models and that are tested with larger samples, as is the case in this study, and thus should be given primacy to other indicators (Hair, Black, Babin, & Anderson, 2010). The χ2/df and RMSEA are below the maximum recommended values of 5 and 0.07, respectively, and CFI is above the minimum threshold of 0.90 ( Hair et al., 2010). With reference to the indications of Fornell and Larcker (1981), Hair et al. (2010) and Netemeyer, Bearden, and Sharma (2003), the previous results and those presented in Table 2 ; Table 3 suggest that the scales used in the measurement model have the following psychometric properties: unidimensionality, because the model has an adequate overall fit; 1reliability, given that all constructs have an average variance extracted (AVE) above the minimum recommended value of 0.50, as well as a composite reliability (CR) and a Cronbachs alpha above 0.70; convergent validity, given that the factorial loadings of the free parameters are statistically significant at the 0.05 level (|t-value| ≥ 1.96), the standardized loadings are higher than the minimum value of 0.50 and the AVE and the CR are higher than the minimum recommended values; discriminant validity, because the square root of each constructs AVE is larger than its correlations (in modulus) with other constructs; nomological validity, since that are statistically significant and in the right direction all correlations related to the hypothesis formulated in the research model.
| Construct | Item | Loading | t-value | Standardized loading | AVE | CR | Cronbachs alpha |
|---|---|---|---|---|---|---|---|
| PRIV | PRIV1 | 1.000 | 0.925 | 0.836 | 0.953 | 0.938 | |
| PRIV2 | 0.947 | 95.293 | 0.876 | ||||
| PRIV3 | 0.979 | 98.265 | 0.905 | ||||
| PRIV4 | 1.026 | 95.028 | 0.949 | ||||
| TRUST | TRUST1 | 1.000 | 0.784 | 0.702 | 0.875 | 0.845 | |
| TRUST2 | 1.184 | 23.377 | 0.928 | ||||
| TRUST3 | 1.012 | 24.790 | 0.793 | ||||
| RISK | RISK1 | 1.000 | 0.842 | 0.522 | 0.883 | 0.862 | |
| RISK2 | 0.846 | 28.751 | 0.712 | ||||
| RISK3 | 0.875 | 29.791 | 0.736 | ||||
| RISK4 | 1.017 | 43.486 | 0.856 | ||||
| RISK5 | 0.731 | 22.824 | 0.615 | ||||
| RISK6 | 0.733 | 22.606 | 0.617 | ||||
| RISK7 | 0.755 | 23.499 | 0.636 | ||||
| PU | PU1 | 1.000 | 0.768 | 0.619 | 0.867 | 0.860 | |
| PU2 | 1.038 | 29.049 | 0.797 | ||||
| PU3 | 1.003 | 28.435 | 0.770 | ||||
| PU4 | 1.058 | 35.962 | 0.812 | ||||
| PEU | PEU1 | 1.000 | 0.891 | 0.752 | 0.923 | 0.905 | |
| PEU2 | 1.034 | 55.952 | 0.922 | ||||
| PEU3 | 0.876 | 16.940 | 0.780 | ||||
| PEU4 | 0.974 | 17.291 | 0.868 | ||||
| PBC | PBC1 | 1.000 | 0.930 | 0.879 | 0.967 | 0.956 | |
| PBC2 | 1.001 | 51.135 | 0.931 | ||||
| PBC3 | 1.009 | 82.187 | 0.939 | ||||
| PBC4 | 1.021 | 65.842 | 0.949 | ||||
| ATT | ATT1 | 1.000 | 0.882 | 0.791 | 0.938 | 0.922 | |
| ATT2 | 1.043 | 56.384 | 0.921 | ||||
| ATT3 | 1.063 | 68.461 | 0.938 | ||||
| ATT4 | 0.919 | 41.664 | 0.811 | ||||
| INT | INT1 | 1.000 | 0.945 | 0.880 | 0.956 | 0.945 | |
| INT2 | 0.985 | 33.035 | 0.932 | ||||
| INT3 | 0.992 | 25.026 | 0.937 | ||||
| PRIV | TRUST | RISK | PU | PEU | PBC | ATT | INT | |
|---|---|---|---|---|---|---|---|---|
| PRIV | 0.914 | |||||||
| TRUST | −0.200 | 0.838 | ||||||
| RISK | 0.219 | −0.207 | 0.722 | |||||
| PU | −0.266 | 0.214 | 0.028 | 0.787 | ||||
| PEU | −0.467 | 0.349 | −0.223 | 0.385 | 0.867 | |||
| PBC | −0.419 | 0.357 | −0.177 | 0.416 | 0.806 | 0.937 | ||
| ATT | −0.573 | 0.414 | −0.361 | 0.411 | 0.686 | 0.601 | 0.889 | |
| INT | −0.447 | 0.293 | −0.227 | 0.464 | 0.614 | 0.561 | 0.692 | 0.938 |
Note: Values below the diagonal represent correlations between constructs; values of the diagonal are the square root of AVE; all correlations are significant at 0.001 (two-tailed).
Regarding the structural model, the results evidence its appropriate overall fit (χ2 = 1684.758, p = 0.000; χ2/df = 3.517; RMSEA = 0.0529; CFI = 0.984). Analysing the estimated parameters of structural relationships, from Fig. 1, we conclude that, in all cases, the standardized loadings have a signal compatible with the direction of the relationships proposed in the research model and are statistically significant at the 0.05 level (|t-value| ≥ 1.96). As such, we accept all the hypotheses proposed in the research model.
The variance explained (R2) of the beliefs that mediate the relationship between privacy concerns and attitude vary between 0.044 for trust and 0.703 for perceived ease of use. Together, the determinants of attitude towards the use of EC and intention to use EC explain, respectively, 60.2% and 60.6% of its variance, values that can be considered acceptable.
Table 4 summarizes the direct, indirect and total effects among latent variables. Through the data presented we conclude that in 8 of 16 hypothesis there are indirect effects which are all statistically significant at a 0.05 level (|t-value| ≥ 1.96). We can extract the same conclusion about the 9 indirect effects that do not involve the hypotheses of the research model, which are described at the end of the table.
| Hypothesis | Independent variable | Dependent variable | Direct effect | Indirect effect | Total effect | |||
|---|---|---|---|---|---|---|---|---|
| Loading | t-value | Loading | t-value | Loading | t-value | |||
| H1a) | PRIV | TRUST | −0.210 | −5.525 | −0.210 | −5.525 | ||
| H1b) | PRIV | RISK | 0.190 | 4.735 | 0.039 | 3.491 | 0.230 | 5.709 |
| H2 | TRUST | RISK | −0.186 | −3.905 | −0.186 | −3.905 | ||
| H3a) | PRIV | PU | −0.131 | −2.875 | −0.185 | −7.012 | −0.316 | −8.319 |
| H3b) | PRIV | PEU | −0.177 | −5.575 | −0.327 | −10.972 | −0.505 | −15.000 |
| H4 | PEU | PU | 0.366 | 7.403 | 0.366 | 7.403 | ||
| H5 | PRIV | PBC | −0.379 | −11.262 | −0.060 | −4.691 | −0.439 | −13.501 |
| H6 | TRUST | PBC | 0.287 | 7.933 | 0.287 | 7.933 | ||
| H7 | PBC | PEU | 0.745 | 21.000 | 0.745 | 21.000 | ||
| H8a) | TRUST | ATT | 0.144 | 4.702 | 0.172 | 7.941 | 0.316 | 9.625 |
| H8b) | RISK | ATT | −0.229 | −7.818 | −0.229 | −7.818 | ||
| H9a) | PU | ATT | 0.190 | 4.872 | 0.190 | 4.872 | ||
| H9b) | PEU | ATT | 0.537 | 11.702 | 0.069 | 4.925 | 0.607 | 7.323 |
| H10 | PU | INT | 0.195 | 5.235 | 0.102 | 5.131 | 0.297 | 14.733 |
| H11 | PBC | INT | 0.188 | 4.434 | 0.296 | 9.885 | 0.484 | 12.783 |
| H12 | ATT | INT | 0.537 | 11.469 | 0.537 | 11.469 | ||
| PRIV | ATT | −0.414 | −13.469 | −0.414 | −13.469 | |||
| PRIV | INT | −0.367 | −12.875 | −0.367 | −12.875 | |||
| TRUST | PU | 0.078 | 4.996 | 0.078 | 4.996 | |||
| TRUST | PEU | 0.214 | 7.170 | 0.214 | 7.170 | |||
| TRUST | INT | 0.239 | 9.886 | 0.239 | 9.886 | |||
| RISK | INT | −0.123 | −6.314 | −0.123 | −6.314 | |||
| PEU | INT | 0.397 | 9.629 | 0.397 | 9.629 | |||
| PBC | PU | 0.273 | 7.181 | 0.273 | 7.181 | |||
| PBC | ATT | 0.452 | 14.588 | 0.452 | 14.588 | |||
We highlight for their magnitude the indirect effects of hypotheses (H3a), (H3b), (H8a) and (H11) which are higher than their direct effects. In these cases, as well as in the remaining four of lesser magnitude, indirect effects reinforce the direct effects, resulting in total effects that confirmed with more robustness the acceptance of the underlying hypotheses.
Overall we can state that the presence of indirect effects increased by about 27% the average of the absolute values of the standardized weights of structural relations, which thus rises from 0.293 to 0.372.
The significant indirect effect of privacy concern on attitude suggests the mediating effects of trust, perceived risk, perceived usefulness, perceived ease of use, and perceived behavioural control. In turn, the significant indirect effect of privacy concern on behaviour intention suggests the mediating effects of the last constructs, and attitude.
We assess the level of mediation comparing the original model with the models that added the direct effect of privacy concern on attitude and on purchasing intention. Regarding Table 5, we can conclude that the revised model with the direct impact of privacy concern on attitude have a significant decrease in χ2(Δχ2 = 33.883, df = 1, p < 0.001), an improvement in model fit and a significant direct effect for the PRIV→ATT relationship. The indirect effect for the last relationship is significant and represents the majority of the total effects. The remaining direct relationships of this model are also significant. These findings suggest that there is a partial mediation of the relationship between privacy concerns and attitude.
| Original model | Model with direct effect PRIV→ATT | Model with direct effect PRIV→INT | |
|---|---|---|---|
| χ2 | 1684.758 | 1650.875 | 1683.571 |
| df | 479 | 478 | 478 |
| p value | <0.001 | <0.001 | <0.001 |
| RMSEA | 0.0529 | 0.0522 | 0.0530 |
| CFI | 0.984 | 0.984 | 0.984 |
| Standardized loading | PRIV→ATT|INT | PRIV→ATT | PRIV→INT |
|---|---|---|---|
| Direct effect | – | −0.277* | −0.086* |
| Indirect effect | −0.414*|−0.367* | −0.322* | −0.344* |
| Total effect | −0.414*|−0.367* | −0.599* | −0.430* |
- . Statistically significant at 0.05 level.
The revised model with the direct impact of privacy concerns on purchasing intention had a non-significant decrease in χ2(Δχ2 = 1.187, df = 1, p = 0.276) and almost the same model fit. Although by the rule of parsimony the original model is the preferred (James, Mulaik, & Brett, 2006), we analyzed the direct and indirect effects for the PRIV→INT relationship and concluded that both were significant. The remaining direct relationships of this revised model are also significant. These results suggest that there is a partial mediation of the relationship between privacy concerns and purchasing intention.
6. Discussion and conclusions
Broadly speaking, the results confirm the acceptance of all proposed hypotheses and the overall validation of the research model.
Looking at each hypothesis of the research model we can conclude that privacy concerns on the Internet has a negative impact on various beliefs about the use of EC, such as trust, perceived usefulness, perceived ease of use, and perceived behavioural control, and a positive impact on perceived risk. These findings corroborate the results obtained in studies of Eastlick et al. (2006), Pavlou and Fygenson (2006), Van Slyke et al. (2006), and Venkatesh et al. (2002) in the context of online shopping behaviour. The strongest direct effect of privacy concerns is felt on perceived behavioural control and the strongest total effect is felt on perceived ease of use.
Regarding the relations between beliefs, we should evidence the negative impact of trust on perceived risk and on perceived behavioural control. Moreover, this last construct has a positive effect on perceived ease of use and on perceived usefulness. These findings confirmed the results obtained in the studies of Ha and Stoel (2009), Pavlou (2003), and Pavlou and Fygenson (2006) in the context of online shopping behaviour, and Venkatesh (2000), in the context of technology adoption.
This study also evidenced that the attitude towards the use of the EC suffers the impact of diverse beliefs, which is positive in the case of trust, perceived usefulness and perceived ease of use, and negative in the case of perceived risk. These findings reinforce the results obtained in the studies of Fenech and O’Cass (2001), Ha and Stoel (2009), and Pavlou and Fygenson (2006) in the context of online shopping behaviour. The strongest direct and total effect on attitude towards the use of EC is exercised by perceived ease of use.
Finally, the results obtained in this study allow us to conclude that the intention to use the EC suffers the positive impact of perceived usefulness, perceived behavioural control and attitude. These findings corroborate the results obtained in the works of Lwin and Williams (2003), and Pavlou (2003) in the context of online shopping behaviour. The strongest direct and total effect on the intention to use EC is exercised by attitude.
It is important to emphasize that this study produces empirical evidence that supports the acceptance of innovative hypotheses in the context of EC that have been proposed in the research model: privacy concerns have a negative impact on perceived usefulness, and on perceived ease of use, and perceived behavioural control has a positive impact on perceived ease of use.
The most important theoretical contribution of this study is creation and validation of an empirical model that explains how privacy concerns on the Internet exerts its impact on the intention to shop online. This model aimed to overcome a literature gap, which corresponded to a certain subalternization of the role of privacy concern in the context of EC, since this variable has been incorporated into explanatory models of online shopping that are, in essence, focused on trust or perceived risk. Moreover, the published studies focuses mainly on the direct effect of privacy concern on online purchasing intention or online purchasing behaviour, not providing a sufficiently robust theoretical framework to explain how privacy concerns exerts its influence on consumer behaviour relevant variables that precede pre-behavioural or behavioural constructs. In fact, no work highlighted privacy concerns to the point of being the only exogenous variable in the context of an explanatory model of online shopping intention.
The originality of the model is also reflected on the concatenation of various theories and models of consumer behaviour widely used in the literature (theories of trust and risk, TAM and TPB) in mediating the relationship between privacy concerns and behaviour intention.
Another theoretical contribution is the reinforcement of privacy theories, to the extent that results highlighted the significant impact of this variable on consumers intention to buy online, through its connection to the trust-risk model, the TAM and the TPB, which behave as mediators of that relationship. In fact, the results demonstrated the connection of privacy concerns to the trust-risk model, through its significant direct negative impact on trust and its positive impact on perceived risk. Moreover, the results evidenced the connection of privacy concerns to the TPB, through its significant direct negative impact on the perceived behavioural control. Finally, the results showed the connection of privacy concerns to the TAM, via its significant direct negative impact on the perceived usefulness and perceived ease of use.
From the standpoint of theoretical contributions, it is also important to note that the results suggest the possibility of connecting trust and risk theories, TPB and TAM at the level of consumer beliefs through perceived behavioural control and their integration within a broader model. In fact, the connection between the trust-risk model and the TPB is ensured by the significant positive direct effect of trust on perceived behavioural control. In turn, the link between the TPB and the TAM is achieved through the significant direct positive impact of perceived behavioural control on perceived ease of use. In this context, perceived behavioural control behaves as a pivot variable that ensures the connection between the trust-risk model, the TPB and the TAM.
In terms of managerial contributions, we highlight that EC sites should have a special care about its users’ personal information privacy, given the negative impact that privacy concerns have on online purchasing intention. We would leave as suggestions for online retailers:
- Development of a privacy policy that is clear and understandable for consumers, which scrupulously observe the principles of collection of personal information, user control over the information collected and awareness about how the information will be used;
- Placement of this privacy policy in a conspicuous place on the website and its periodic disclosure to the database of registered users in order to strengthen their positive beliefs;
- Communication of the privacy policy of the site to each new registered user, through a call of attention in the registration process and an e-mail containing this information;
- The implementation of the privacy policy through privacy practices that are compatible. It is not enough to set a good privacy policy, it must be implemented and make it known;
- Certification of websites by external entities, such as TRUSTe, Trust Guard, or BBBOnline, ensuring the possibility of using the so-called privacy seals.
This study has some limitations. First, we can point to the use of a non-random sample, which impairs the ability to generalize the results. However, we were careful to collect a nationwide sample from the largest Portuguese online panel. Moreover, the study opted not to include actual online purchase behaviour in the research model explaining only purchase intention. Despite this, based on studies grounded in the TRA, TPB and TAM, we believe that online purchasing intention is a significant determinant of online purchasing behaviour. In addition, the questionnaire contained questions about the EC sites in general, which may contain some ambiguity to the respondent, in that their response may vary depending on the site in question. Finally, in order not to excessively increase the size of the questionnaire, we chose to use unidimensional scales for measuring privacy concern, trust and perceived risk, which can be conceptualized as multidimensional constructs. Although we believe that the scales used capture the major dimensions of those constructs, the use of multidimensional scales could lead to different results from those obtained in this study.
As recommendations for future research we propose: the construction and validation of a model on the determinants of privacy concerns; to conduct a longitudinal study that includes online purchasing behaviour in the research; the application of the proposed research model in different countries and online sectors.
Appendix 1. Measurement scales
| Scales | Items | References |
|---|---|---|
| PRIV | I am concerned that the information I submit on the Internet could be misused. I am concerned that a person can find private information about me on the Internet. I am concerned about submitting information on the Internet, because of what others might do with it. I am concerned about submitting information on the Internet, because it could be used in a way I did not foresee. | Dinev and Hart (2006) |
| TRUST | The web retailers are trustworthy. The web retailers keep their promises and commitments. The web retailers keep their customers best interests in mind. | Pavlou (2003) |
| RISK | Shopping online is risky. Providing credit card information online is risky. Providing personal information (i.e., social security number and mothers maiden name) online is risky. Purchasing items online is risky. Providing my and phone number online is risky. Registering online is risky. It is riskier to shop online for a product than to shop offline for it. | Schlosser et al. (2006) |
| PU | Shopping on the internet allows me to save money. Shopping on the internet allows me to save time. Shopping on the Internet provides me access to a wide variety of products and services. For me, it is useful to make purchases on the Internet. | Park et al. (2004) |
| PEU | I learned easily to shop on the Internet. Shopping on the internet is for me a clear and understandable process. I become easily skilful at shopping on the Internet. For me, its easy to shop on the Internet. | Koufaris (2002) |
| PBC | The extent of knowledge that I feel I have in making my purchase decision is sufficient. The extent of control that I feel I have in making my purchase decision is sufficient. The extent of resources that I feel I have at my disposal in making my purchase decision is sufficient. The extent of self-confidence that I feel I have in making my purchase decision is sufficient. | Song and Zahedi (2005) |
| ATT | I like making purchases on the Internet. Making purchases on the Internet is a wise idea. Making purchases on the Internet is a good idea. Making purchases on the Internet is a pleasant idea. | Lim and Dubinsky (2005) |
| INT | Its likely that I make purchases on the Internet in the future. Its possible that I make purchases on the Internet in the future. Its probable that I make purchases on the Internet in the future. | Schlosser et al. (2006) |
References
- Ajzen, 1991 I. Ajzen; The theory of planned behaviour; Organizational Behavior and Human Decision Processes, 50 (1991), pp. 179–211
- Benbasat and Barki, 2007 I. Benbasat, H. Barki; Quo Vadis TAM; Journal of the Association for Information Systems, 8 (4) (2007), pp. 211–218
- Brown and Muchira, 2004 M. Brown, R. Muchira; Investigating the relationship between Internet privacy concerns and online purchase behaviour; Journal of Electronic Commerce Research, 5 (1) (2004), pp. 62–70
- Chen and Barnes, 2007 Y. Chen, S. Barnes; Initial trust and online buyer behaviour; Industrial Management & Data Systems, 107 (1) (2007), pp. 21–36
- Crespo et al., 2009 A. Crespo, I. Bosque, M. Sánchez; The influence of perceived risk on Internet shopping behavior: A multidimensional perspective; Journal of Risk Research, 12 (2) (2009), pp. 259–277
- Culnan and Armstrong, 1999 M. Culnan, P. Armstrong; Information privacy concerns procedural fairness, and impersonal trust: An empirical investigation; Organization Science, 10 (1) (1999), pp. 104–115
- Davis, 1989 F. Davis; Perceived usefulness, perceived ease of use, and user acceptance of information technology; MIS Quarterly, 13 (3) (1989), pp. 319–340
- Davis et al., 1989 F. Davis, R. Bagozzi, P. Warshaw; User acceptance of technology: A comparison of two theoretical models; Management Sciences, 35 (8) (1989), pp. 982–1003
- Davis et al., 1992 F. Davis, R. Bagozzi, P. Warshaw; Extrinsic and intrinsic motivation to use computers in the workplace; Journal of Applied Social Psychology, 22 (14) (1992), pp. 1111–1132
- Dinev and Hart, 2006 T. Dinev, P. Hart; Internet privacy concerns and social awareness as determinants of intention to transact; International Journal of Electronic Commerce, 10 (2) (2006), pp. 7–31
- Eastlick et al., 2006 M. Eastlick, S. Lotz, P. Warrington; Understanding online B-to-C relationships: An integrated model of privacy concerns, trust, and commitment; Journal of Business Research, 59 (8) (2006), pp. 877–886
- Dinev et al., 2006a T. Dinev, M. Bellotto, P. Hart, V. Russo, I. Serra, C. Colautti; Internet users’ privacy concerns and beliefs about government surveillance: An exploratory study of differences between Italy and the United States; Journal of Global Information Management, 14 (4) (2006), pp. 57–93
- Dinev et al., 2006b T. Dinev, M. Bellotto, P. Hart, V. Russo, I. Serra, C. Colautti; Privacy calculus model in e-commerce: A study of Italy and the United States; European Journal of Information Systems, 15 (4) (2006), pp. 389–402
- Eurostat, 2014 Eurostat; E-Commerce by individuals and enterprises; (2014) Retrieved from http://epp.eurostat.ec.europa.eu/portal/page/portal/information_society/data/database
- Fenech and O’Cass, 2001 T. Fenech, A. O’Cass; Internet users’ adoption of Web retailing: User and product dimensions; Journal of Product and Brand Management, 10 (6) (2001), pp. 361–381
- Fornell and Larcker, 1981 C. Fornell, D. Larcker; Evaluating structural equation models with unobservable variables and measurement error; Journal of Marketing Research, 18 (1) (1981), pp. 39–50
- Gerbing and Anderson, 1988 D. Gerbing, J. Anderson; An updated paradigm for scale development incorporating unidimensionality and its assessment; Journal of Marketing Research, 25 (2) (1988), pp. 186–192
- Gillin, 2000 D. Gillin; The federal trade commission and Internet privacy; Marketing Research, 12 (3) (2000), pp. 39–41
- Glover and Benbasat, 2011 S. Glover, I. Benbasat; A comprehensive model of perceived risk of E-commerce transactions; International Journal of Electronic Commerce, 15 (2) (2011), pp. 47–78
- Ha and Stoel, 2009 S. Ha, L. Stoel; Consumer E-shopping acceptance: Antecedents in a technology acceptance model; Journal of Business Research, 62 (5) (2009), pp. 565–571
- Hair et al., 2010 J. Hair, W. Black, B. Babin, R. Anderson; Multivariate data analysis: A global perspective; Pearson, Upper Saddle River, NJ (2010)
- Hoffman et al., 1999 D. Hoffman, T. Novak, M. Peralta; Information privacy in the marketspace: Implications for the commercial uses of anonymity on the Web; Information Society, 15 (2) (1999), pp. 129–139
- James et al., 2006 L.R. James, S.A. Mulaik, J.M. Brett; A tale of two methods; Organizational Research Methods, 9 (2) (2006), pp. 233–244
- Jarvenpaa et al., 2000 S. Jarvenpaa, N. Tractinsky, M. Vitale; Consumer trust in an Internet store; Information Technology and Management, 1 (1) (2000), pp. 45–71
- Jones, 1991 M. Jones; Privacy: A significant marketing issue for the 1990s; Journal of Public Policy and Marketing, 10 (1) (1991), pp. 133–148
- Kim et al., 2009 D. Kim, D. Ferrin, H. Rao; Trust and satisfaction, two stepping stones for successful e-Commerce relationships: A longitudinal exploration; Information Systems Research, 20 (2) (2009), pp. 237–257
- Kim et al., 2010 J. Kim, W. Kim, S. Park; Consumer perceptions on web advertisements and motivation factors to purchase in the online shopping; Computers in Human Behavior, 26 (5) (2010), pp. 1208–1222
- Koufaris, 2002 M. Koufaris; Applying the technology acceptance model and flow theory to online consumer behavior; Information Systems Research, 13 (2) (2002), pp. 205–223
- Lee and Turban, 2001 M.K. Lee, E. Turban; A trust model for consumer internet shopping; International Journal of electronic commerce, 6 (1) (2001), pp. 75–91
- Li et al., 2011 H. Li, R. Sarathy, H. Xu; The role of affect and cognition on online consumers’ decision to disclose personal information to unfamiliar online vendors; Decision Support Systems, 51 (3) (2011), pp. 434–445
- Liao et al., 2011 C. Liao, C. Liu, K. Chen; Examining the impact of privacy, trust and risk perceptions beyond monetary transactions: An integrated model; Electronic Commerce Research and Applications, 10 (6) (2011), pp. 702–715
- Lim and Dubinsky, 2005 H. Lim, A. Dubinsky; The theory of planned behavior in e-commerce: Making a case for interdependencies between salient beliefs; Psychology and Marketing, 22 (10) (2005), pp. 833–855
- Lim, 2003 N. Lim; Consumers’ perceived risk: Sources versus consequences; Electronic Consumer Research and Applications, 2 (2003), pp. 216–228
- Liu et al., 2005 C. Liu, J. Marchewka, J. Lu, C. Yu; Beyond concern – a privacy-trust-behavioral intention model of electronic commerce; Information Management, 42 (2) (2005), pp. 289–304
- Lwin and Williams, 2003 M. Lwin, J. Williams; A model integrating the multidimensional development theory of privacy and theory of planned behaviour to examine fabrication of information online; Marketing Letters, 14 (4) (2003), pp. 257–272
- Malhotra et al., 2004 N. Malhotra, S. Kim, J. Agarwal; Internet users information privacy concerns (IUIPC): The construct the scale, and a causal model; Information Systems Research, 15 (4) (2004), pp. 336–355
- McCole et al., 2010 P. McCole, E. Ramsey, J. Williams; Trust considerations on attitudes towards online purchasing: The moderating effect of privacy and security concerns; Journal of Business Research, 63 (9–10) (2010), pp. 1018–1024
- McKnight et al., 2002 D. McKnight, V. Choudhury, C. Kacmar; The impact of initial consumer trust on intentions to transact with a Web site: A trust building model; Journal of Strategic Information Systems, 11 (3–4) (2002), pp. 297–323
- McKnight et al., 1998 D. McKnight, L. Cummings, N. Chervany; Initial trust formation in new organizational relationships; Academy of Management Review, 23 (3) (1998), pp. 473–490
- Midha, 2012 V. Midha; Impact of consumer empowerment on online trust: An examination across genders; Decision Support Systems, 54 (1) (2012), pp. 198–205
- Miyazaki and Fernandez, 2000 A. Miyazaki, A. Fernandez; Internet privacy and security: An examination of online retailer disclosures; Journal of Public Policy and Marketing, 19 (1) (2000), pp. 54–61
- Moorman et al., 1992 C. Moorman, G. Zaltman, R. Deshpande; Relationship between providers and users of market research: The dynamics of trust within and between organizations; Journal of Marketing Research, 29 (3) (1992), pp. 314–328
- Netemeyer et al., 2003 R. Netemeyer, W. Bearden, S. Sharma; Scaling procedures: Issues and applications; Sage, Thousand Oaks. CA (2003)
- Palvia, 2009 P. Palvia; The role of trust in e-commerce relational exchange: A unified model; Information & Management, 46 (4) (2009), pp. 213–220
- Park et al., 2004 J. Park, D. Lee, J. Ahn; Risk-focused e-commerce adoption model: A cross country study; Journal of Global Information Technology Management, 7 (2) (2004), pp. 6–30
- Pavlou and Fygenson, 2006 P. Pavlou, M. Fygenson; Understanding and predicting electronic commerce adoption: An extension of the theory of planned behavior; MIS Quarterly, 30 (1) (2006), pp. 115–143
- Pavlou, 2003 P. Pavlou; Consumer acceptance of electronic commerce: Integrating trust and risk with the Technology Acceptance Model; International Journal of Electronic Commerce, 7 (3) (2003), pp. 101–134
- Podsakoff et al., 2003 P.M. Podsakoff, S.B. MacKenzie, J.Y. Lee, N.P. Podsakoff; Common method biases in behavioral research: A critical review of the literature and recommended remedies; Journal of Applied Psychology, 88 (5) (2003), pp. 879–903
- Schlosser et al., 2006 A. Schlosser, T. White, S. Lloyd; Converting web site visitors into buyers: How web site investment increases consumer trusting beliefs and online purchase intentions; Journal of Marketing, 70 (2) (2006), pp. 133–148
- Sheehan and Hoy, 2000 K. Sheehan, M. Hoy; Dimensions of privacy concern among online consumers; Journal of Public Policy and Marketing, 19 (1) (2000), pp. 62–73
- Smith et al., 1996 H. Smith, S. Milberg, S. Burke; Information privacy: Measuring individuals’ concerns about organizational practices; MIS Quarterly, 20 (2) (1996), pp. 167–196
- Song and Zahedi, 2005 J. Song, F. Zahedi; Web design in e-commerce: A belief reinforcement model; Management Science, 51 (8) (2005), pp. 1219–1235
- Taylor et al., 2009 D. Taylor, D. Davis, R. Jillapalli; Privacy concern and online personalization: The moderating effects of information control and compensation; Electronic Commerce Research, 9 (3) (2009), pp. 203–223
- Teo and Liu, 2007 T. Teo, J. Liu; Consumer trust in e-commerce in the United States, Singapore and China; Omega: International Journal of Management Science, 35 (1) (2007), pp. 22–38
- Van Dyke et al., 2007 T. Van Dyke, V. Midha, H. Nemati; The effect of consumer privacy empowerment on trust and privacy concerns in e-commerce; Electronic Markets, 17 (1) (2007), pp. 68–81
- Van Slyke et al., 2006 C. Van Slyke, J. Shim, R. Johnson, J. Jiang; Concern for information privacy and online consumer purchasing; Journal of the Association for Information Systems, 7 (6) (2006), pp. 415–444
- Venkatesh, 2000 V. Venkatesh; Determinants of perceived ease of use: Integrating control, intrinsic motivation, and emotion into the technology acceptance model; Information Systems Research, 11 (4) (2000), pp. 342–365
- Venkatesh et al., 2002 V. Venkatesh, S. Cheri, M. Morris; User acceptance of enablers in individual decision making about technology: Towards an integrated model; Decision Sciences, 33 (2) (2002), pp. 297–316
- Westin, 1967 A. Westin; Privacy and freedom; Atheneum, New York (1967)
Notes
1. Prior to confirmatory factor analysis was performed an exploratory factor analysis whose results gave support to the unidimensionality of all scales, since were retained eight distinct factors, each one comprises the items of each scale (KMO = 0.923; Bartletts test p-value = 0.000; Variance explained = 74.653%; Communalities > 0.5; Loadings > 0.7).
Document information
Published on 12/06/17
Submitted on 12/06/17
Licence: Other
Share this document
Keywords
claim authorship
Are you one of the authors of this document?